Edge-Powered Drone Detection System
AIRSPACE SECURITY GAP
Modern unmanned threats penetrate security perimeters with increasing sophistication, evading traditional detection systems.
Aviation Incidents
monthly unauthorized drone reports near airports (FAA)
FAA UAS Sightings ReportTHE EYE SYSTEM
Distributed intelligence platform that transforms optical sensors into threat detection nodes.
SYSTEM ARCHITECTURE
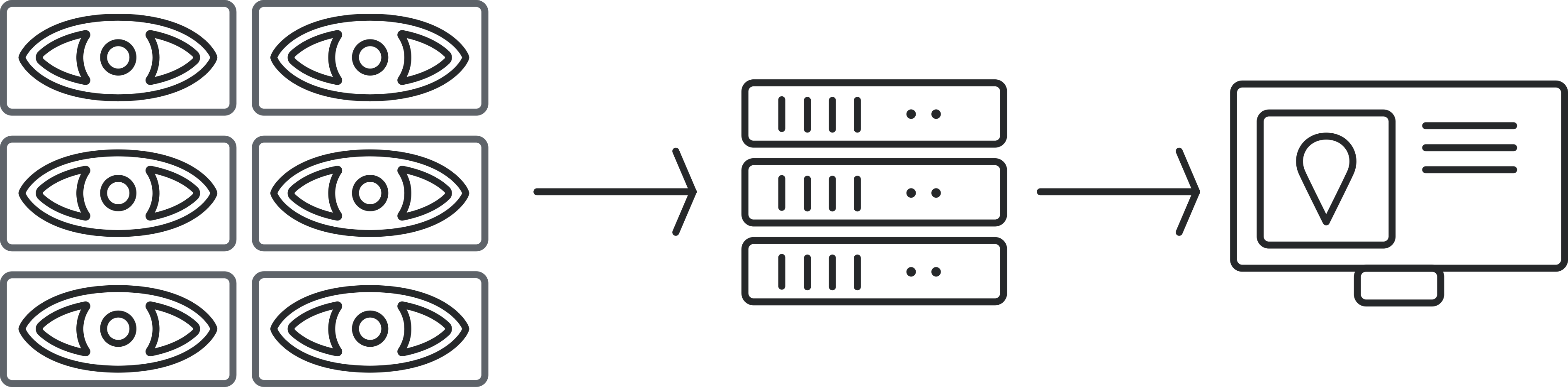
Edge Devices
Smartphones or other cameras equipped with AI model for local image analysis.
Central Communication System
Collects data from all connected edge devices across the operational environment.
Management Platform
Web application with interactive map, alerts, and incident overview interface.
OPERATIONAL FRAMEWORK
THE EYE employs a streamlined process from detection to actionable intelligence.
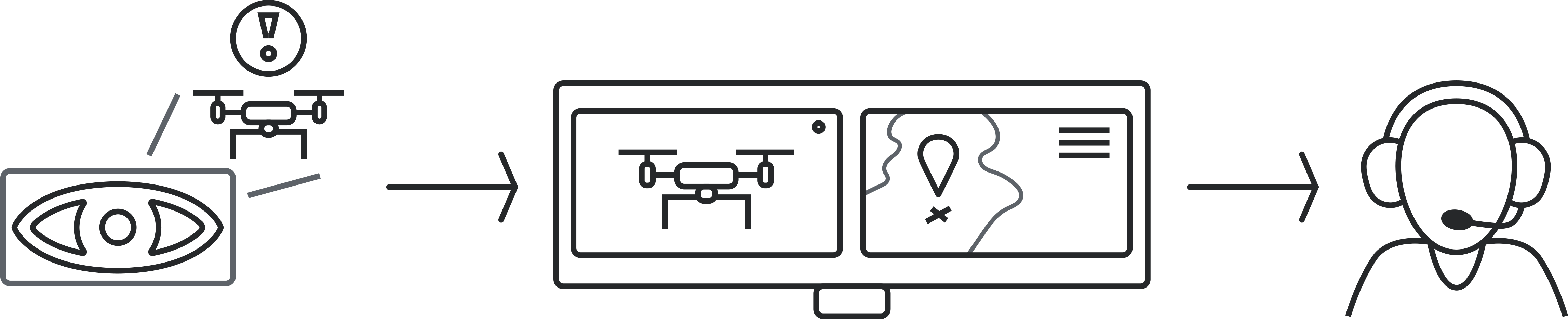
WORKFLOW PROCESS
Deploy
Position detection nodes at strategic vantage points across the operational area.
Analyze
Edge processing conducts continuous visual analysis of surrounding airspace.
Identify
Computer vision algorithm flags aerial objects and classifies threat profile.
Transmit
Alert data sent to command platform with location and evidence packet.
Act
Command center receives actionable intelligence for immediate response.
Deploy
Position detection nodes at strategic vantage points across the operational area.
Analyze
Edge processing conducts continuous visual analysis of surrounding airspace.
Identify
Computer vision algorithm flags aerial objects and classifies threat profile.
Transmit
Alert data sent to command platform with location and evidence packet.
Act
Command center receives actionable intelligence for immediate response.
TECHNOLOGY
Edge processing and visual intelligence designed for security applications.
Real-time Threat Identification
Computer vision technology identifies threats and tracks movement patterns regardless of radio emissions or communication methods.
Distributed Architecture
Modular system extends detection capabilities across any operational environment with seamless node integration.
Edge Processing Intelligence
Advanced classification algorithms at the edge reduce latency and maintain functionality in challenging environments.
MULTI-PLATFORM INTEGRATION
The strategic advantage of THE EYE system lies in its deployment flexibility. By leveraging our proprietary secure software layer, virtually any optical device can be transformed into a defense-grade detection node, enabling rapid scalability across various hardware platforms.
Tactical deployment via standard smartphones and tablets with encrypted secure container technology to maintain operational security at the edge.
Integration with existing perimeter security infrastructure through secure gateway modules, enhancing defense posture without additional hardware investment.
Purpose-built hardened detection units with multi-spectrum sensors for forward deployment in high-threat environments with extended detection range.
Starting price per device
Threat detection latency
Continuous operation
Regular over-the-air updates
OPERATIONAL DOMAINS
THE EYE adapts to diverse security challenges with exceptional versatility.
Military & Defense
Tactical deployment in high-threat environments with minimal infrastructure requirements.
Critical Infrastructure
Integrated protection for essential facilities against unauthorized aerial incursions.
Border & Perimeter Security
Extended surveillance capabilities for large-scale perimeter monitoring applications.
Airports
Comprehensive airspace monitoring and threat detection for air traffic safety.
SECURE YOUR AIRSPACE
Join us in developing the next generation of airspace security solutions.